-
WANTED: Happy members who like to discuss audio and other topics related to our interest. Desire to learn and share knowledge of science required. There are many reviews of audio hardware and expert members to help answer your questions. Click here to have your audio equipment measured for free!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Stop browser trackers once and for all
- Thread Starter
- #42
Google is forced to change their language… after a class action lawsuit.
Good riddance.
Good riddance.
Ze Frog
Addicted to Fun and Learning
- Joined
- Jan 4, 2024
- Messages
- 666
- Likes
- 767
Tor isn't nearly as secure as it once was, but then it won't be as it was originally designed for U.S military and intelligence channels, so they will know how to workaround it despite public release being heavily modified.Vivaldi browser is a tracker by itself, lol. And can't protect you from fingerprinting either.
Until it doesn't.
This whole browser tweaking topic is completely useless. If you really want websites to stop tracking you — use Tor Browser. Every browser trick you enable makes you stand out more, not less.
CreepJS
abrahamjuliot.github.io
Regarding browsers, they all spy on you, it's just a matter of which nation or organisation they are spying for. Until recently this was all rather benign, but in the last three years and events and the resulting propaganda, I think it's become a deep concern as people might not want an organisation or government to know they are looking beyond the mainstream for information out of fear of possible persecution. VPN is probably more important in that regard, but even a VPN isn't really anonymity, more just a bypass of blocks. Let's face it, technology and science has for decades been commercialised and weaponized by states, companies or organisations. What ever we have access to now you can be sure such things have a way around the supposed workarounds. To believe we are even allowed thing's like VPN's etc if they truly made a user invisible is just fantasy.
Most of the time those mentioned above are very not likely to investigate each person constantly. You would likely have to be deemed a threat through crime or inciting viewpoints that don't conform to the expected line to quite a point before any action was to be initiated, or at least we'd like to hope so.
- Thread Starter
- #44
Interesting…

 www.bleepingcomputer.com
www.bleepingcomputer.com
Brave to end 'Strict' fingerprinting protection as it breaks websites

Brave to end 'Strict' fingerprinting protection as it breaks websites
Brave Software has announced plans to deprecate the 'Strict' fingerprinting protection mode in its privacy-focused Brave Browser because it causes many sites to function incorrectly.
- Joined
- Feb 23, 2016
- Messages
- 21,522
- Likes
- 39,237
That is certainly what I found using it. Strict was effectively useless except with those few sites not trying to track you. Same with no script. No script is a little less aggressive than Strict mode in Brave I'd say.Interesting…
Brave to end 'Strict' fingerprinting protection as it breaks websites

Brave to end 'Strict' fingerprinting protection as it breaks websites
Brave Software has announced plans to deprecate the 'Strict' fingerprinting protection mode in its privacy-focused Brave Browser because it causes many sites to function incorrectly.www.bleepingcomputer.com
Sad state of affairs that more or less you cannot use the web unless they get to track you. Richard Stallman was right as he often is, but I don't think I want to be him.
- Thread Starter
- #47
On a related now, I'm diving deeper into the ad-blocking via DNS sinkhole approach.
For example, even with my go-to recommendation of disabling Windows telemetry/tracking of using ShupUp10++, that's just the first step in eliminating telemetry/tracking by Microsoft.
This program uses dozens of registry tweaks to disable various Windows settings that both visible (in the system settings) and not visible to the user (in the registry).
So instead of figuring out all these tweaks yourself, which is just silly, it's a good thing that someone created a program like ShutUp10++.
Even after running ShutUp10++, there's a lot of traffic that still initiates connections from Windows to various domains.
A more layered approach needs to be taken.
ShutUp10++ is the 1st step, but DNS sinkhole will be the second layer (short of firewalling all outbound/inbound traffic, which I don't recommend).
Btw, I've tried the extreme approach of blocking all network traffic that's outgoing from your Windows machine, with the free "Malwarebytes Windows Firewall Control".
It's essentially a firewall on steroids.
Link here.

This program is stopping all traffic first and then whitelisting apps as they initiate connections. With this whitelisting approach, you'll get constantly alerted to every single connection in the beginning and less so overtime.
Plus, most people don't understand what each traffic is doing, so this firewall approach isn't very practical.
Anyway, let's get back to DNS analysis.
On MacOS, the equivalent program to "Malwarebytes Windows Firewall Control" would be either "Little Snitch" (paid) and "Lulu" (free), which also function like a firewall blocking/allowing network traffic.
Lulu can't be combined with a DNS ad-list, which is a shame.
Little Snitch can be combined with a DNS ad-list, which is great.
But Little Snitch isn't free (it's like $50), unlike AdGuard for MacOS (which is like $5).
Little Snitch shows you which process initiated the DNS connection, which AdGuard for MacOS doesn't do unfortunately.
So for anyone diving deeper, you'll need a software like Little Snitch. For anyone with a set-and-forget approach, AdGuard for MacOS works better.
But let's focus on Windows now.
First, let's look at what traffic your Windows is attempting to make via DNS lookups.
I use the free application by NirSoft called DNSLookupView.
Link here.
The reason I'm using this program over others is that it shows your process name and process path (the path in your Windows directory) that the DNS lookup came from. This is important to narrow down the source of the lookup. AdGuard for Windows, for example, doesnt show this information.
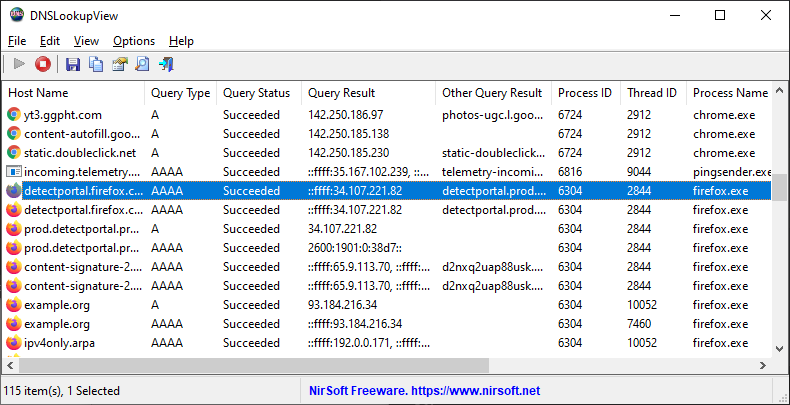
Steps after you download it:
I've placed the executable in a directory, that I know I won't delete.
Steps after you open it:
1. Move the most important columns to the front
Right click on any columns and move these to the front:
#1 Time
#2 Process Path
#3 Host Name
I've left the rest of the columns as is, since they can be logged into a log file for later analysis, but without needing them right now.
2. Made sure that even if I close the program, it still runs in the background
Go to Options, enable 'put icon on tray'
3. Made sure it scrolls to new entries each time
Go to options, enable 'automatically scroll down to new items'
4. To make sure it starts logging, as soon as the program is open
Go to options, enable 'automatically start dns tracing'
5. To save the file automatically to your computer
Go to options, advanced options, enable 'add dns queries to the following file' and input a file, like 'c:\users\dns.txt'
This is an eye-opening experience to see how much DNS lookups your computer is attempting to make.
I say attempting, since if you have an ad-blocker at the host level or at the network level, it will be stopped at that point.
Host level:
- uBlock Origin for all browsers
- AdGuard for Windows
- PortMaster for Windows
- AdGuard for MacOS
- Little Snitch + (DNS ad-list) for MacOS
- AdGuard for mobile (iOS and Android)
- etc
Network level:
- Pi-hole
- AdGuard Home
- etc
This is important to understand:
- Every browser application that you test this one will be first filtered by your ad-blocker. Meaning, if you install uBlock Origin for any browser, and then look at DNSLookupView, it won't log all DNS lookups. That's because uBlock Origin is blocking these domain lookups so fast that it doesnt reach DNSLookupView. So the only way is to disable your ad-blocker and then look at traffic via DNSLookupView.
- Every other application (other than your browsers) will show DNS traffic normally, so that will always be logged into DNSLookupView.
The effectiveness of your ad-blocker will be dictated by the ad-lists that you're using.
By the way, so far I've found 2 websites with the most # of ads that are blocked by my ad-blockers:
These are cnn.com and foxnews.com
For example, just me going to cnn.com using a browser with no ad-blockers, will result in 300 DNS lookups visible by DNSLookupView. If we consider A and AAAA DNS lookups as a single entry, which DNSLookupView logs for every domain. That means 150 domains were queried by DNS upon visiting cnn.com. I'm guessing 1/2 to 1/3 of these domains are ad/privacy tracking. Anyway, it's a lot.
The real problem is how to figure out which DNS traffic is normal vs which DNS traffic is telemetry/privacy tracking.
There's no way a user will make their own ad-list, since each person will take years to do this.
Luckily, there's plenty of ads/privacy ad-lists that people have compiled and are constantly updating.
So it's really a matter of choosing a specific DNS ad-list.
I have my preferences for DNS ad-lists that I prefer over others. Stacking them will result in more ads/privacy/telemetry being blocked. But at some point, if you stack too many, a few applications will break so you'll need to disable ad-lists temporary to see if the applications works again. Then whitelist the domains that broke something previously.
My current approach was to find a single ad-list that works without breaking anything (day-to-day) and still provides a good enough approach to blocking ads/privacy/trackers.
I found the 'AdGuard DNS ad-list' to be the current one that works across all platforms without breaking anything that I need.
This is the ad-list that I can recommend to friends and family and never have to think about it breaking something.
So let's analyze all programs and whether they can use this ad-list:
Lots of options.
What do you need to do, beyond installing any of these apps?
Also, blocking YouTube ads with DNS-based blocker is impossible. So you need to have a browser with uBlock Origin, which is doing both cosmetic and HTTP filtering, which a DNS-based blockers can't handle.
But as soon as you enable uBlock Origin and then try to analyze DNS domains blocked by your ad-list for your favorite DNS-filtering application (that I've listed above), uBlock Origin will be too quick, meaning a lot of traffic won't be visible to DNS-based blockers. That's just something you need to understand, when analyzing DNS logs. So, always disable browser ad-list extension when analyzing logs, since DNS-based application would then show you all the results.
All of DNS entries are being filtered at all times, regardless of where im at or what device i'm using:
1. uBlock Origin for all browsers to do cosmetic and HTTP filtering.
Benefits:
- for blocking YouTube ads
- removing blank spaces where ads used to be
- very fast, so your DNS server doesnt need to filter all DNS requests from your browser, since your CPU of your device will handle it before reaching your DNS filter
2. AdGuard Home for network level (aka DNS) filtering
3. AdGuard for mobile, for when I'm using cellular data. Alternatively, you could run a VPN that always tunnels traffic when you're using your cellular connection to your home's connection. That way, you're protected via AdGuard Home.
Anyway, I need to write a full guide on this to be more in depth.
For example, even with my go-to recommendation of disabling Windows telemetry/tracking of using ShupUp10++, that's just the first step in eliminating telemetry/tracking by Microsoft.
This program uses dozens of registry tweaks to disable various Windows settings that both visible (in the system settings) and not visible to the user (in the registry).
So instead of figuring out all these tweaks yourself, which is just silly, it's a good thing that someone created a program like ShutUp10++.
Even after running ShutUp10++, there's a lot of traffic that still initiates connections from Windows to various domains.
A more layered approach needs to be taken.
ShutUp10++ is the 1st step, but DNS sinkhole will be the second layer (short of firewalling all outbound/inbound traffic, which I don't recommend).
Btw, I've tried the extreme approach of blocking all network traffic that's outgoing from your Windows machine, with the free "Malwarebytes Windows Firewall Control".
It's essentially a firewall on steroids.
Link here.

This program is stopping all traffic first and then whitelisting apps as they initiate connections. With this whitelisting approach, you'll get constantly alerted to every single connection in the beginning and less so overtime.
Plus, most people don't understand what each traffic is doing, so this firewall approach isn't very practical.
Anyway, let's get back to DNS analysis.
On MacOS, the equivalent program to "Malwarebytes Windows Firewall Control" would be either "Little Snitch" (paid) and "Lulu" (free), which also function like a firewall blocking/allowing network traffic.
Lulu can't be combined with a DNS ad-list, which is a shame.
Little Snitch can be combined with a DNS ad-list, which is great.
But Little Snitch isn't free (it's like $50), unlike AdGuard for MacOS (which is like $5).
Little Snitch shows you which process initiated the DNS connection, which AdGuard for MacOS doesn't do unfortunately.
So for anyone diving deeper, you'll need a software like Little Snitch. For anyone with a set-and-forget approach, AdGuard for MacOS works better.
But let's focus on Windows now.
First, let's look at what traffic your Windows is attempting to make via DNS lookups.
I use the free application by NirSoft called DNSLookupView.
Link here.
The reason I'm using this program over others is that it shows your process name and process path (the path in your Windows directory) that the DNS lookup came from. This is important to narrow down the source of the lookup. AdGuard for Windows, for example, doesnt show this information.

Steps after you download it:
I've placed the executable in a directory, that I know I won't delete.
Steps after you open it:
1. Move the most important columns to the front
Right click on any columns and move these to the front:
#1 Time
#2 Process Path
#3 Host Name
I've left the rest of the columns as is, since they can be logged into a log file for later analysis, but without needing them right now.
2. Made sure that even if I close the program, it still runs in the background
Go to Options, enable 'put icon on tray'
3. Made sure it scrolls to new entries each time
Go to options, enable 'automatically scroll down to new items'
4. To make sure it starts logging, as soon as the program is open
Go to options, enable 'automatically start dns tracing'
5. To save the file automatically to your computer
Go to options, advanced options, enable 'add dns queries to the following file' and input a file, like 'c:\users\dns.txt'
This is an eye-opening experience to see how much DNS lookups your computer is attempting to make.
I say attempting, since if you have an ad-blocker at the host level or at the network level, it will be stopped at that point.
Host level:
- uBlock Origin for all browsers
- AdGuard for Windows
- PortMaster for Windows
- AdGuard for MacOS
- Little Snitch + (DNS ad-list) for MacOS
- AdGuard for mobile (iOS and Android)
- etc
Network level:
- Pi-hole
- AdGuard Home
- etc
This is important to understand:
- Every browser application that you test this one will be first filtered by your ad-blocker. Meaning, if you install uBlock Origin for any browser, and then look at DNSLookupView, it won't log all DNS lookups. That's because uBlock Origin is blocking these domain lookups so fast that it doesnt reach DNSLookupView. So the only way is to disable your ad-blocker and then look at traffic via DNSLookupView.
- Every other application (other than your browsers) will show DNS traffic normally, so that will always be logged into DNSLookupView.
The effectiveness of your ad-blocker will be dictated by the ad-lists that you're using.
By the way, so far I've found 2 websites with the most # of ads that are blocked by my ad-blockers:
These are cnn.com and foxnews.com
For example, just me going to cnn.com using a browser with no ad-blockers, will result in 300 DNS lookups visible by DNSLookupView. If we consider A and AAAA DNS lookups as a single entry, which DNSLookupView logs for every domain. That means 150 domains were queried by DNS upon visiting cnn.com. I'm guessing 1/2 to 1/3 of these domains are ad/privacy tracking. Anyway, it's a lot.
The real problem is how to figure out which DNS traffic is normal vs which DNS traffic is telemetry/privacy tracking.
There's no way a user will make their own ad-list, since each person will take years to do this.
Luckily, there's plenty of ads/privacy ad-lists that people have compiled and are constantly updating.
So it's really a matter of choosing a specific DNS ad-list.
I have my preferences for DNS ad-lists that I prefer over others. Stacking them will result in more ads/privacy/telemetry being blocked. But at some point, if you stack too many, a few applications will break so you'll need to disable ad-lists temporary to see if the applications works again. Then whitelist the domains that broke something previously.
My current approach was to find a single ad-list that works without breaking anything (day-to-day) and still provides a good enough approach to blocking ads/privacy/trackers.
I found the 'AdGuard DNS ad-list' to be the current one that works across all platforms without breaking anything that I need.
This is the ad-list that I can recommend to friends and family and never have to think about it breaking something.
So let's analyze all programs and whether they can use this ad-list:
| OS | Name |
| Windows | AdGuard |
| Windows | PortMaster |
| MacOS | AdGuard |
| MacOS | Little Snitch |
| Firewall level | Pi-Hole |
| Firewall level | AdGuard Home |
| Mobile (both iOS and Android OS) | AdGuard |
Lots of options.
What do you need to do, beyond installing any of these apps?
| Name | What needs to be done after installation? |
| AdGuard (all platforms) (free to install, lifetime license is $5 to use advanced features) | Simply enable 'AdGuard DNS' ad-list in the GUI, under 'DNS protection' |
| PortMaster for Windows (free) | Go to settings, scroll down to 'filter lists', disable all default ad-lists (to start clean), enable the 'AdGuardDNS list by ray' (which is part of Mixed Ads/Trackers/Malware dropdown) |
| Little Snitch for MacOS (paid) | In settings set "Silent Mode — Allow Connections" (which allows all traffic) You need to manually add this ad-list, go to "File > New Rule Group Subscription": Make sure it's 'activated', then save. This just blocks the ad-list DNS traffic, which makes Little Snitch function like AdGuard. |
| Pi-Hole (v5 current) (free) | Go to group management, "adlists", then manually add this: |
| Pi-Hole (v6 upcoming) (free) | Go to group management, "adlists", then manually add this: |
Also, blocking YouTube ads with DNS-based blocker is impossible. So you need to have a browser with uBlock Origin, which is doing both cosmetic and HTTP filtering, which a DNS-based blockers can't handle.
But as soon as you enable uBlock Origin and then try to analyze DNS domains blocked by your ad-list for your favorite DNS-filtering application (that I've listed above), uBlock Origin will be too quick, meaning a lot of traffic won't be visible to DNS-based blockers. That's just something you need to understand, when analyzing DNS logs. So, always disable browser ad-list extension when analyzing logs, since DNS-based application would then show you all the results.
All of DNS entries are being filtered at all times, regardless of where im at or what device i'm using:
1. uBlock Origin for all browsers to do cosmetic and HTTP filtering.
Benefits:
- for blocking YouTube ads
- removing blank spaces where ads used to be
- very fast, so your DNS server doesnt need to filter all DNS requests from your browser, since your CPU of your device will handle it before reaching your DNS filter
2. AdGuard Home for network level (aka DNS) filtering
3. AdGuard for mobile, for when I'm using cellular data. Alternatively, you could run a VPN that always tunnels traffic when you're using your cellular connection to your home's connection. That way, you're protected via AdGuard Home.
Anyway, I need to write a full guide on this to be more in depth.
Last edited:
- Joined
- Feb 23, 2016
- Messages
- 21,522
- Likes
- 39,237
- Thread Starter
- #49
I took a look at W10Privacy (link) (free app for Windows), similar to ShutUp10++ in purpose.
Both are closed-source, but trusted in the community.
If you go to Telemetry tab, you'll see:
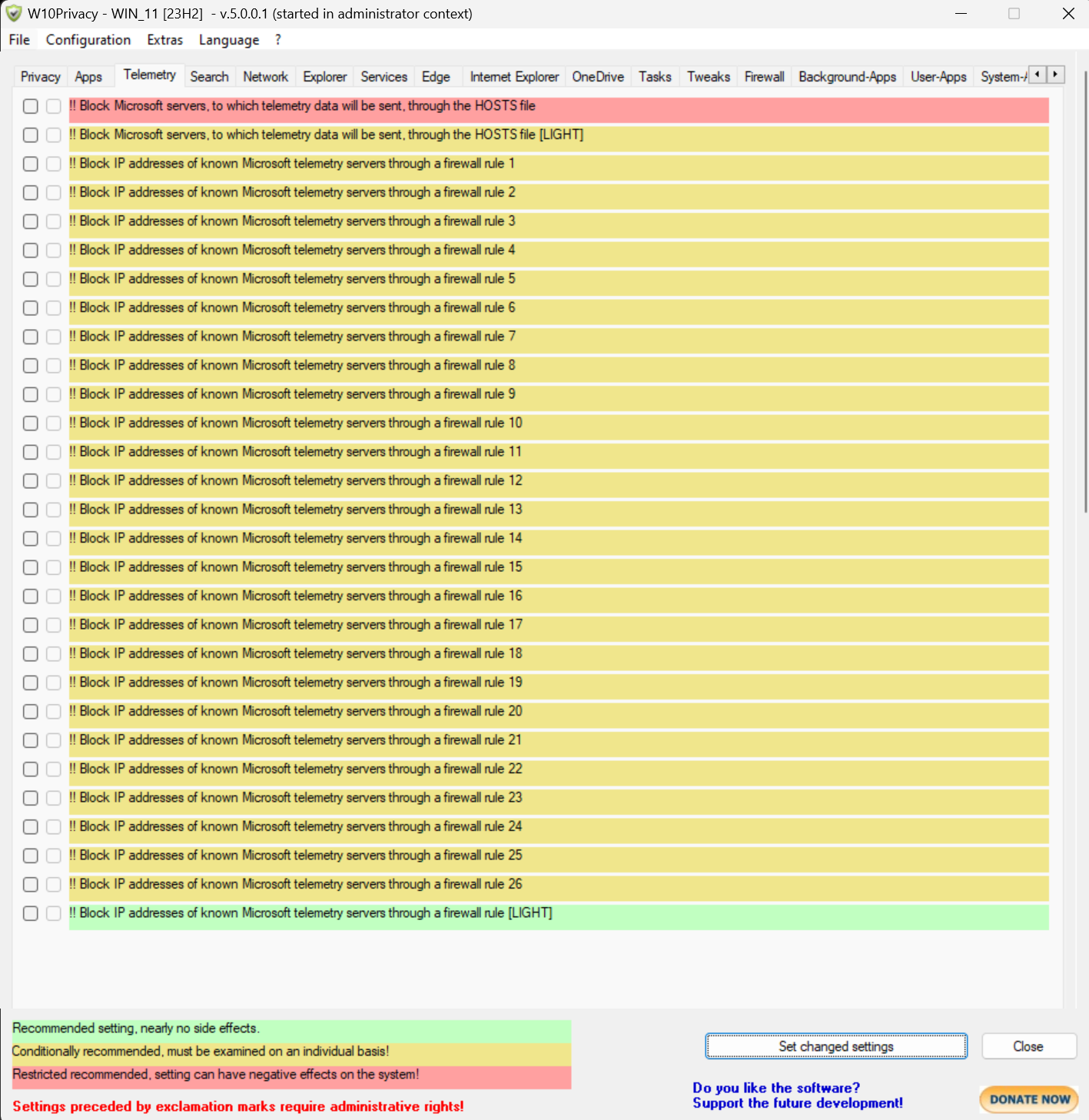
There's 2 things that it does:
1. add hostnames to your hosts file, which makes it a DNS sinkhole.
2. add firewall rules for Microsoft domains and/or IPs
Let's take a look at the firewall rules it creates:
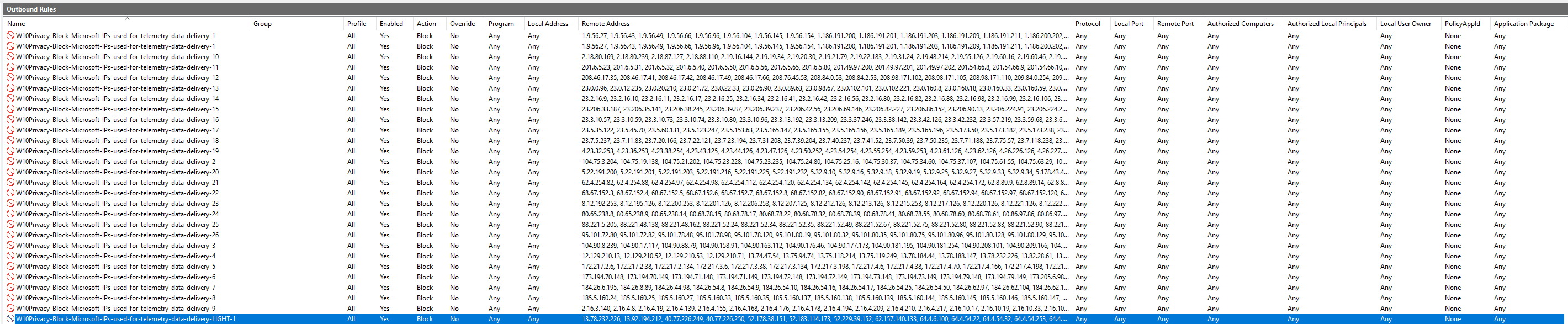
One thing is clear, it only adds IP addresses.
The problem with this approach is 2 fold:
1. It won't block hostnames, which means if Microsoft changes the IP for a given domain, this adlist will eventually become absolete. Unless you keep downloading W10Privacy and re-enable this rule. In other words, this approach will become a hassle if Microsoft keeps changing IPs.
2. Even if blocking IPs via this firewall rule will work, the problem is that this becomes invisible to the user. Which means you can't look at this log very easily. Not to mention, ublocking domains becomes a hassle as well, since you have to edit this hosts file.
Let's take a look at the hosts based approach.
It will create a DNS sinkhole for various Microsoft domains in your "C:\Windows\System32\drivers\etc"
Open 'hosts' with notepad to see.
So, let's test W10Privacy's first HOSTS LIGHT (shown as the yellow highlight):
So, let's test W10Privacy's second HOSTS FULL (shows as the red highlight).
Quick summary:
"Hosts Light" file added 92 domain entries that will block various Microsoft domains.
"Hosts Full" file added 285 domain entries that will block various Microsoft domains.
But I still don't like using HOSTS file for a DNS sinkhole, since you can't see the log file very easily.
I prefer using any of the DNS-based filtering systems I mentioned above.
In this example, let's use the network-based filter called "AdGuard Home".
Too bad "AdGuard Home" doesnt allow me to input a local .txt as the ad-list.
So I had to upload this HOSTS FULL file to pastebin.
Then created an unlisted "paste exposure", named it "W10Privacy Hosts Full" and saved.
Once it created the custom url, you still can't use this to paste.
So you have to get the raw file, here's the raw file I created:
https://pastebin.com/raw/SJ5wytn5
Now you can import this into 'AdGuard Home'.
Seeing how this W10Privacy application is very popular, I don't know why nobody imported this ad-list into it's own ad-list to be shared online yet?
Maybe i'm the first, haha.
Now you can see the full log, since every DNS lookup is now logged properly.
Of course, I verified that "Windows Update" still works as indented, since that's critical app that must keep working.
I combine this with my 1 ad-list that doesnt break anything, 'AdGuard DNS' ad-list to block 3rd-party known ad-lists.
Overall, my approach for Windows 10/11 is now:
1. Run ShutUp10++, Apply recommended settings. Restart pc.
This blocks the majority of windows configurable settings related to privacy.
2. Setup either a host-based or network-based DNS filtering system.
Host level:
- uBlock Origin for all browsers
- AdGuard for Windows
- PortMaster for Windows
- AdGuard for MacOS
- Little Snitch + (DNS ad-list) for MacOS
- AdGuard for mobile (iOS and Android)
- etc
Network level:
- Pi-hole
- AdGuard Home
- etc
This ensures that I can start to use ad-lists, in order to sinkhole DNS entries.
3. Once installed, start blocking Microsoft telemetry domains, by adding this adlist:
https://pastebin.com/raw/SJ5wytn5
Which is just a copy of W10Privacy's Hosts Full list, that I manually created, since I couldnt find this copy online.
4. Add 2nd ad-list that doesnt break any major service, but blocks ads/tracking/telemetry from known servers.
This is the 'AdGuard DNS' ad-list, which I've shows above on how to enable for different systems.
5. Using a host-based adblocker like uBlock Origin is still a requirement for all system browsers, since it uses cosmetic and HTTP filtering that DNS-filtering cannot handle.
For now, I can't think of another more layered approach that's more effective at blocking ads/telemetry for both OS and network level.
I guess an AI-based approach could be layered on top of this, at some point in the future.
Microsoft is doing this with Windows Defender for Endpoint, but that's a costly subscription solution. Plus it works for malware, more than for Microsoft-owned domains.
The solutions I use above literally takes a few minutes and almost free (I guess $5 licesne for AdGuard is almost free).
My personal solution includes:
1. uBlock Origin for all browsers, even Brave, which already comes with ad-blocking built in, which works already. I just like the control of uBlock Origin on top of that.
2. Network level, DNS-based approach. I can recommend 'AdGuard Home' for the easiest solution. I've also tested the upcoming Pi-hole version 6, which can now work with adlists that AdGuard Home can use, since the current version of Pi-hole v5 is only limited to domain-based ad-lists. Once it comes out, I might be going back to Pi-hole. For now, i don't like to use buggy software, so i'm sticking with AdGuard Home.
4. Using those 2 ad-lists.
You can start to stack other ad-lists, but as I've warned before. Websites and applications will start to break. So good luck to you.
Peace!
Both are closed-source, but trusted in the community.
If you go to Telemetry tab, you'll see:
There's 2 things that it does:
1. add hostnames to your hosts file, which makes it a DNS sinkhole.
2. add firewall rules for Microsoft domains and/or IPs
Let's take a look at the firewall rules it creates:
One thing is clear, it only adds IP addresses.
The problem with this approach is 2 fold:
1. It won't block hostnames, which means if Microsoft changes the IP for a given domain, this adlist will eventually become absolete. Unless you keep downloading W10Privacy and re-enable this rule. In other words, this approach will become a hassle if Microsoft keeps changing IPs.
2. Even if blocking IPs via this firewall rule will work, the problem is that this becomes invisible to the user. Which means you can't look at this log very easily. Not to mention, ublocking domains becomes a hassle as well, since you have to edit this hosts file.
Let's take a look at the hosts based approach.
It will create a DNS sinkhole for various Microsoft domains in your "C:\Windows\System32\drivers\etc"
Open 'hosts' with notepad to see.
So, let's test W10Privacy's first HOSTS LIGHT (shown as the yellow highlight):
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
0.0.0.0 0.0.0.0 # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 asimov-win.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 candycrushsoda.king.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 co4.telecommand.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs11.wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs1137.wpc.gammacdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5-eap.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 diagnostics.support.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.microsoft-hohm.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.search.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onecollector.cloudapp.aria.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 reports.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 self.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 services.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe1.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.update.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 survey.watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tele.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.appex.bing.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.remoteapp.windowsazure.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tsfe.trafficshaping.dsp.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.ppe.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
0.0.0.0 0.0.0.0 # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 asimov-win.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 candycrushsoda.king.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 co4.telecommand.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs11.wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs1137.wpc.gammacdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5-eap.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 diagnostics.support.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.microsoft-hohm.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.search.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onecollector.cloudapp.aria.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 reports.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 self.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 services.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe1.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.update.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 survey.watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tele.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.appex.bing.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.remoteapp.windowsazure.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tsfe.trafficshaping.dsp.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.ppe.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
So, let's test W10Privacy's second HOSTS FULL (shows as the red highlight).
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
0.0.0.0 0.0.0.0 # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0001.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0001.dc-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0002.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0003.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0003.dc-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0004.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0005.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0006.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0007.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0008.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0009.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0010.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0011.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0012.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.rad.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.ads1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.ads2.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.ads2.msads.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ac3.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ad.doubleclick.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 adnexus.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 adnxs.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ads.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ads1.msads.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ads1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 aidps.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 aka-cdn-ns.adtech.de # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 answers.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 apac1.notify.windows.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 appex-rf.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 api.cortana.ai # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 api.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 api.onedrive.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 apps.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 arc.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 arc.msn.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ars.smartscreen.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 asimov-win.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 auth.gfx.ms # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 az361816.vo.msecnd.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 az512334.vo.msecnd.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 b.rad.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 b.ads2.msads.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 b.ads1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 bingads.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 browser.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 browser.pipe.aria.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 bs.serving-sys.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 bubblewitch3mobile.king.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c-0001.dc-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c1.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cache.datamart.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 candycrush.king.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cdn.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cdn.content.prod.cms.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cdn.onenote.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cds26.ams9.msecn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 checkappexec.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 client-office365-tas.msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 client-s.gateway.messenger.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 clientconfig.passport.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 client.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 co2.sls.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 co4.telecommand.telemetry.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 compatexchange.cloudapp.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 compatexchange1.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 config.edge.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 config.teams.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 continuum.dds.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 corp.sts.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 corpext.msitadfs.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs1.wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs11.wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs1137.wpc.gammacdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.displaycatalog.md.mp.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.licensing.md.mp.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db3aqu.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5-dspcdn.tlu.dl.delivery.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5-eap.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5p.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5p.wns.notify.windows.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 diagnostics.support.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 displaycatalog.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dm3p.wns.notify.windows.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dmd.metaservices.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dmd.metaservices.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dns.msftncsi.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 e-0009.e-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 e-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ec.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu-v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu-v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 europe.smartscreen-prod.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 evoke-windowsservices-tas.msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.microsoft-hohm.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.search.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 finance.services.appex.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 foodanddrink.tile.appex.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 flex.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 flightingservicewus.cloudapp.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 fs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.msn.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 global.sam.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 go.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 h1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 h2.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 hk2.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 hk2.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 i1.services.social.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 i1.services.social.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 iecvlist.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ieonlinews.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ieonlinews.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 inference.location.live.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 insiderservice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ip5.afdorigin-prod-am02.afdogw.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ipv4.login.msa.akadns6.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 iriscoremetadataprod.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 lb1.www.ms.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 live.rads.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 location-inference-westus.cloudapp.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 m.adnxs.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 m.hotmail.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 mediaredirect.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 mobile.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 mobile.pipe.aria.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msagfx.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msftncsi.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msnbot-65-55-108-23.search.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msntest.serving-sys.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 nexus.officeapps.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 nexusrules.officeapps.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ocos-office365-s2s.msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 officecdn.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 officecdn.microsoft.com.edgesuite.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 officeclient.microsoft.comoneclient.sfx.ms # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onecollector.cloudapp.aria.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ow1.res.office365.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 pre.footprintpredict.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 preview.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 pricelist.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 prod.nexusrules.live.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 query.prod.cms.rt.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 rad.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 rad.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 redir.metaservices.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 register.cdpcs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 reports.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ris.api.iris.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ris-prod-atm.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s-0001.s-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s.gateway.messenger.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s0.2mdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s2s.config.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 schemas.microsoft.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 secure.adnxs.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 secure.flashtalking.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 self.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 service.weather.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 services.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-win-ppe.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sfdataservice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sg2p.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 share.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sO.2mdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 spynet2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 spynetalt.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 spyneteurope.microsoft.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ssw.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 static.2mdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe1.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.update.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 survey.watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 t.checkappexec.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tele.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.appex.bing.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.remoteapp.windowsazure.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tile-service.weather.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tsfe.trafficshaping.dsp.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ui.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 umwatsonc.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 t.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tk2.plt.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 uhf.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 urs.smartscreen.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us-v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us-v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.configsvc1.live.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 view.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vip5.afdorigin-prod-am02.afdogw.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 w.apprep.smartscreen.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wallet.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.ppe.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wd-prod-cp-us-east-2-fe.eastus.cloudapp.azure.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wdcp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wdcpalt.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 web.vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont.apps.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont.apps.microsoft.com.edgesuite.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont1.apps.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont2.apps.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 x.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
0.0.0.0 0.0.0.0 # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0001.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0001.dc-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0002.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0003.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0003.dc-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0004.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0005.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0006.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0007.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0008.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0009.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0010.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0011.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-0012.a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.rad.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.ads1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.ads2.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 a.ads2.msads.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ac3.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ad.doubleclick.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 adnexus.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 adnxs.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ads.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ads1.msads.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ads1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 aidps.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 aka-cdn-ns.adtech.de # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 alpha.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 answers.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 apac1.notify.windows.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 appex-rf.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 api.cortana.ai # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 api.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 api.onedrive.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 apps.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 arc.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 arc.msn.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ars.smartscreen.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 asimov-win.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 auth.gfx.ms # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 az361816.vo.msecnd.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 az512334.vo.msecnd.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 b.rad.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 b.ads2.msads.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 b.ads1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 bingads.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 browser.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 browser.pipe.aria.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 bs.serving-sys.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 bubblewitch3mobile.king.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c-0001.dc-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 c1.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cache.datamart.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 candycrush.king.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ceuswatcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cdn.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cdn.content.prod.cms.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cdn.onenote.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cds26.ams9.msecn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 checkappexec.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 choice.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 client-office365-tas.msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 client-s.gateway.messenger.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 clientconfig.passport.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 client.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 co2.sls.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 co4.telecommand.telemetry.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 compatexchange.cloudapp.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 compatexchange1.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 config.edge.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 config.teams.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 continuum.dds.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 corp.sts.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 corpext.msitadfs.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs1.wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs11.wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cs1137.wpc.gammacdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.displaycatalog.md.mp.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.licensing.md.mp.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 cy2.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db3aqu.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5-dspcdn.tlu.dl.delivery.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5-eap.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5p.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 db5p.wns.notify.windows.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 diagnostics.support.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 displaycatalog.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dm3p.wns.notify.windows.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dmd.metaservices.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dmd.metaservices.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 dns.msftncsi.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 e-0009.e-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 e-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eaus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ec.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu-v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 eu-v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 europe.smartscreen-prod.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 evoke-windowsservices-tas.msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.microsoft-hohm.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.search.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 feedback.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 finance.services.appex.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 foodanddrink.tile.appex.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 flex.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 flightingservicewus.cloudapp.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 fs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.bing.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 g.msn.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.settings-win.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 geo.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 global.sam.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 go.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 h1.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 h2.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 hk2.settings.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 hk2.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 i1.services.social.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 i1.services.social.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 iecvlist.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ieonlinews.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ieonlinews.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 inference.location.live.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 insiderservice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ip5.afdorigin-prod-am02.afdogw.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ipv4.login.msa.akadns6.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 iriscoremetadataprod.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 lb1.www.ms.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 live.rads.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 location-inference-westus.cloudapp.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 m.adnxs.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 m.hotmail.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 mediaredirect.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 mobile.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 mobile.pipe.aria.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 modern.watson.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msagfx.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msftncsi.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msnbot-65-55-108-23.search.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 msntest.serving-sys.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 nexus.officeapps.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 nexusrules.officeapps.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 oca.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ocos-office365-s2s.msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 officecdn.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 officecdn.microsoft.com.edgesuite.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 officeclient.microsoft.comoneclient.sfx.ms # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onecollector.cloudapp.aria.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 onesettings-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ow1.res.office365.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 pre.footprintpredict.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 preview.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 pricelist.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 prod.nexusrules.live.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 query.prod.cms.rt.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 rad.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 rad.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 redir.metaservices.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 register.cdpcs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 reports.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ris.api.iris.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ris-prod-atm.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s-0001.s-msedge.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s.gateway.messenger.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s0.2mdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 s2s.config.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 schemas.microsoft.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 secure.adnxs.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 secure.flashtalking.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 self.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 service.weather.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 services.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 settings-win-ppe.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sfdataservice.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sg2p.wns.windows.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 share.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sO.2mdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 spynet2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 spynetalt.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 spyneteurope.microsoft.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ssw.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 static.2mdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe1.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.update.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 statsfe2.ws.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 survey.watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 t.checkappexec.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tele.trafficmanager.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.appex.bing.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.remoteapp.windowsazure.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 telemetry.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tile-service.weather.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tsfe.trafficshaping.dsp.mp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 ui.skype.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 umwatsonc.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 t.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 tk2.plt.msn.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 uhf.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 urs.smartscreen.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us-v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us-v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.configsvc1.live.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 us.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10.vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v10c.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.events.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 v20.vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 view.atdmt.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vip5.afdorigin-prod-am02.afdogw.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.glbdns2.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-bn2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-cy2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-db5.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-hk2.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win.data.metron.live.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 vortex-win-sandbox.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 w.apprep.smartscreen.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wallet.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.live.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.ppe.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 watson.telemetry.microsoft.com.nsatc.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wd-prod-cp-us-east-2-fe.eastus.cloudapp.azure.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wdcp.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wdcpalt.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 web.vortex.data.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wes.df.telemetry.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab01.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 weus2watcab02.blob.core.windows.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont.apps.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont.apps.microsoft.com.edgesuite.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont1.apps.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wscont2.apps.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 wpc.v0cdn.net # Entry added with W10Privacy (www.winprivacy.de)!
0.0.0.0 x.urs.microsoft.com # Entry added with W10Privacy (www.winprivacy.de)!
Quick summary:
"Hosts Light" file added 92 domain entries that will block various Microsoft domains.
"Hosts Full" file added 285 domain entries that will block various Microsoft domains.
But I still don't like using HOSTS file for a DNS sinkhole, since you can't see the log file very easily.
I prefer using any of the DNS-based filtering systems I mentioned above.
In this example, let's use the network-based filter called "AdGuard Home".
Too bad "AdGuard Home" doesnt allow me to input a local .txt as the ad-list.
So I had to upload this HOSTS FULL file to pastebin.
Then created an unlisted "paste exposure", named it "W10Privacy Hosts Full" and saved.
Once it created the custom url, you still can't use this to paste.
So you have to get the raw file, here's the raw file I created:
https://pastebin.com/raw/SJ5wytn5
Now you can import this into 'AdGuard Home'.
Seeing how this W10Privacy application is very popular, I don't know why nobody imported this ad-list into it's own ad-list to be shared online yet?
Maybe i'm the first, haha.
Now you can see the full log, since every DNS lookup is now logged properly.
Of course, I verified that "Windows Update" still works as indented, since that's critical app that must keep working.
I combine this with my 1 ad-list that doesnt break anything, 'AdGuard DNS' ad-list to block 3rd-party known ad-lists.
Overall, my approach for Windows 10/11 is now:
1. Run ShutUp10++, Apply recommended settings. Restart pc.
This blocks the majority of windows configurable settings related to privacy.
2. Setup either a host-based or network-based DNS filtering system.
Host level:
- uBlock Origin for all browsers
- AdGuard for Windows
- PortMaster for Windows
- AdGuard for MacOS
- Little Snitch + (DNS ad-list) for MacOS
- AdGuard for mobile (iOS and Android)
- etc
Network level:
- Pi-hole
- AdGuard Home
- etc
This ensures that I can start to use ad-lists, in order to sinkhole DNS entries.
3. Once installed, start blocking Microsoft telemetry domains, by adding this adlist:
https://pastebin.com/raw/SJ5wytn5
Which is just a copy of W10Privacy's Hosts Full list, that I manually created, since I couldnt find this copy online.
4. Add 2nd ad-list that doesnt break any major service, but blocks ads/tracking/telemetry from known servers.
This is the 'AdGuard DNS' ad-list, which I've shows above on how to enable for different systems.
5. Using a host-based adblocker like uBlock Origin is still a requirement for all system browsers, since it uses cosmetic and HTTP filtering that DNS-filtering cannot handle.
For now, I can't think of another more layered approach that's more effective at blocking ads/telemetry for both OS and network level.
I guess an AI-based approach could be layered on top of this, at some point in the future.
Microsoft is doing this with Windows Defender for Endpoint, but that's a costly subscription solution. Plus it works for malware, more than for Microsoft-owned domains.
The solutions I use above literally takes a few minutes and almost free (I guess $5 licesne for AdGuard is almost free).
My personal solution includes:
1. uBlock Origin for all browsers, even Brave, which already comes with ad-blocking built in, which works already. I just like the control of uBlock Origin on top of that.
2. Network level, DNS-based approach. I can recommend 'AdGuard Home' for the easiest solution. I've also tested the upcoming Pi-hole version 6, which can now work with adlists that AdGuard Home can use, since the current version of Pi-hole v5 is only limited to domain-based ad-lists. Once it comes out, I might be going back to Pi-hole. For now, i don't like to use buggy software, so i'm sticking with AdGuard Home.
4. Using those 2 ad-lists.
You can start to stack other ad-lists, but as I've warned before. Websites and applications will start to break. So good luck to you.
Peace!
Last edited:
Who is reponsable for Brave? I mean, where was developed, in wich country?
I use Brave ,but the most annoying thing is that when ever I look for something in Portuguese it only give Brazilian Portuguese results. And I want Portuguese from Portugal results.
I use Brave ,but the most annoying thing is that when ever I look for something in Portuguese it only give Brazilian Portuguese results. And I want Portuguese from Portugal results.
Last edited:
- Joined
- Jul 21, 2019
- Messages
- 2,469
- Likes
- 3,665
Don't overlook IPv6 networking, because that's another means by which stuff sneaks in. I've seen banner ads being served up via IPv6 addresses. I was surprised to find v6 IP addresses being served up to devices on my home network (via my ISP?) because I had always assumed that v6 wasn't a home network thing. The safe thing that anyone can try is to examine the network settings of one's computer, and simply switch off IPv6 if needed. If all services continue to work as before (which they likely will) then no additional changes are needed.
My home network is set up with Adguard Home, and in addition, I've switched off IPv6 centrally. I consider this the "lazy person's" approach, but initial setup does require some networking know-how.
My home network is set up with Adguard Home, and in addition, I've switched off IPv6 centrally. I consider this the "lazy person's" approach, but initial setup does require some networking know-how.
- Thread Starter
- #52
Network level ad-blockers like Pi-hole and AdGuard Home both support IPV6 ad-lists, so it's already possible to block those ads at the DNS level.
But personally, I haven't personally seen ads come via IPV6 yet.
So if you have a dual stack network (both IPV4 and IPV6), then your firewall wouldn't care since the type of connection comes from the device and the firewall would just allow it.
So yes, IPV6 ad-lists would help there.
Assuming more ads start to come from IPV6 sources as the times goes on, there's a few possible solutions for this problem:
1. If you don't need IPV6 on your firewall, disable it, thereby, the device will communicate via IPV4 instead and you're covered.
2. If you need IPV6 on your firewall, but don't want any firewall rules, just find and add IPV6 ad-lists to your network level ad-blocker. Although, i haven't seen many IPV6 ad-lists yet.
3. If you need IPV6 on your firewall, but don't want to deal with IPV6 ad-lists, then I would implement a redirection rule for DNS queries that are non-IPV4. Meaning, all IPV6 DNS queries will be redirected to Pi-Hole or AdGuard Home, to be processed by it's own IPV4 ad-lists.
But again, I don't find this to be a problem yet.
But personally, I haven't personally seen ads come via IPV6 yet.
So if you have a dual stack network (both IPV4 and IPV6), then your firewall wouldn't care since the type of connection comes from the device and the firewall would just allow it.
So yes, IPV6 ad-lists would help there.
Assuming more ads start to come from IPV6 sources as the times goes on, there's a few possible solutions for this problem:
1. If you don't need IPV6 on your firewall, disable it, thereby, the device will communicate via IPV4 instead and you're covered.
2. If you need IPV6 on your firewall, but don't want any firewall rules, just find and add IPV6 ad-lists to your network level ad-blocker. Although, i haven't seen many IPV6 ad-lists yet.
3. If you need IPV6 on your firewall, but don't want to deal with IPV6 ad-lists, then I would implement a redirection rule for DNS queries that are non-IPV4. Meaning, all IPV6 DNS queries will be redirected to Pi-Hole or AdGuard Home, to be processed by it's own IPV4 ad-lists.
But again, I don't find this to be a problem yet.
- Thread Starter
- #53
The issue I see is with "Rogue Devices".
These devices have hard-coded DNS servers, so when they make a DNS query, it's effectively bypassing your network-level DNS server (like Pi-Hole or AdGuard Home).
Your firewall won't stop these lookups, by default.
You would have to implement a redirection rule on your firewall to redirect all DNS queries that are destined for outside networks, back to your local DNS server (Pi-Hole or AdGuard Home).
I've done with with both pfSense and OpnSense, and works very well.
There's a lot of devices that try to bypass your network level DNS.
Headless IOT devices, for example.
With the redirect rule in place, these rogue devices are no longer rogue.
This problem is worth solving with a redirect rule at the firewall level.
These devices have hard-coded DNS servers, so when they make a DNS query, it's effectively bypassing your network-level DNS server (like Pi-Hole or AdGuard Home).
Your firewall won't stop these lookups, by default.
You would have to implement a redirection rule on your firewall to redirect all DNS queries that are destined for outside networks, back to your local DNS server (Pi-Hole or AdGuard Home).
I've done with with both pfSense and OpnSense, and works very well.
There's a lot of devices that try to bypass your network level DNS.
Headless IOT devices, for example.
With the redirect rule in place, these rogue devices are no longer rogue.
This problem is worth solving with a redirect rule at the firewall level.
Last edited:
- Thread Starter
- #54
This caught my attention:

 www.bleepingcomputer.com
www.bleepingcomputer.com
The researchers suggest iPhone users who want to evade this fingerprinting should disable push notifications entirely.
Here’s the video overview:
Also, Apple is also going to help…
…starting in Spring 2024, apps will be required to declare precisely why they need to use APIs that can be abused for fingerprinting.

iPhone apps abuse iOS push notifications to collect user data
Numerous iOS apps are using background processes triggered by push notifications to collect user data about devices, potentially allowing the creation of fingerprinting profiles used for tracking.
The researchers suggest iPhone users who want to evade this fingerprinting should disable push notifications entirely.
Here’s the video overview:
Also, Apple is also going to help…
…starting in Spring 2024, apps will be required to declare precisely why they need to use APIs that can be abused for fingerprinting.
- Thread Starter
- #55
For iOS users:
With the introduction of iOS 17.3 (which was released 2 days ago), Apple introduced "Stolen Device Protection"
Read the official documentation here:
 support.apple.com
support.apple.com
Which goes a long way in stopping people from easily taking over your Apple account, so I recommend that everyone with an iOS device to enable this ASAP.
It just shocks me how long Apple took to fix this basic security threat.
Better late than never I guess.
If you want to see a video explanation of this problem, how apple fixed it with the "Stolen Device Protection", and what ThioJoe describes as another security risk that Apple doesnt talk about.
It's "Significant Locations" features.
It's found in Settings, Privacy and Security, Location Services, System Services, Significant Locations.
I believe this is enabled by default.
The most shocking thing to me is that Apple marked a total of 299 of these "Significant Locations" on my phone, in the last 3 months.
That's insane!!!!
That means that in any of these locations, the bad guys can bypass my 'Stolen Device Protection' that I just enabled.
Thanks to Apple for creating 'Stolen Device Protection' feature, just to have 300 locations where it can be disabled without my permission. Rolls my eyes.
Then, make sure to 'clear history' to clear these "significant locations".
Anyway, turn off "Significant Locations" and "Clear History", which makes your "Stolen Device Protection" actually useful.
TLDR:
You need to do 3 things to protect your iOS device.
1. Settings, Face ID and Password, Stolen Device Protection, Turn on.
2. Settings, Privacy and Security, Location Services, System Services, Significant Locations. Turn off.
3. Settings, Privacy and Security, Location Services, System Services, Significant Locations. Clear History.
With the introduction of iOS 17.3 (which was released 2 days ago), Apple introduced "Stolen Device Protection"
Read the official documentation here:
About Stolen Device Protection for iPhone - Apple Support
Stolen Device Protection adds a layer of security when your iPhone is away from familiar locations, such as home or work.
Which goes a long way in stopping people from easily taking over your Apple account, so I recommend that everyone with an iOS device to enable this ASAP.
It just shocks me how long Apple took to fix this basic security threat.
Better late than never I guess.
If you want to see a video explanation of this problem, how apple fixed it with the "Stolen Device Protection", and what ThioJoe describes as another security risk that Apple doesnt talk about.
It's "Significant Locations" features.
It's found in Settings, Privacy and Security, Location Services, System Services, Significant Locations.
I believe this is enabled by default.
The most shocking thing to me is that Apple marked a total of 299 of these "Significant Locations" on my phone, in the last 3 months.
That's insane!!!!
That means that in any of these locations, the bad guys can bypass my 'Stolen Device Protection' that I just enabled.
Thanks to Apple for creating 'Stolen Device Protection' feature, just to have 300 locations where it can be disabled without my permission. Rolls my eyes.
Then, make sure to 'clear history' to clear these "significant locations".
Anyway, turn off "Significant Locations" and "Clear History", which makes your "Stolen Device Protection" actually useful.
TLDR:
You need to do 3 things to protect your iOS device.
1. Settings, Face ID and Password, Stolen Device Protection, Turn on.
2. Settings, Privacy and Security, Location Services, System Services, Significant Locations. Turn off.
3. Settings, Privacy and Security, Location Services, System Services, Significant Locations. Clear History.
Last edited:
- Thread Starter
- #56
Re: Importance of ad-blocking
Another day, another company tracking over 5 billion of users worldwide.
A recent investigation by 404 Media has unveiled details about a secretive spy tool called Patternz, which monitors billions of phone profiles through the advertising industry.
Full report:

 www.404media.co
www.404media.co
The Patternz tool provides detailed information about users, including GPS coordinates, frequently visited locations, hobbies, and interests.
Google has known Patternz since at least June 2021, and worked with them until this week, where Google has terminated their account, due to this investigation.
In response to inquiries from 404 Media, Google and another ad firm, PubMatic, have cut off a company linked to the surveillance firm.
The investigation provides one of the clearest examinations yet of how advertisements in ordinary mobile apps can ultimately lead to surveillance by spy firms and their government clients through the real-time bidding data supply chain.
Personal opinion:
Yes, you're being tracked without your consent or knowledge, simply by using services/apps that have ads. These ad networks, then aggregate and correlate information on a worldwide level.
We don't have to make it easy for these companies to gather this data.
If you're not using a host-based and/or network-based ad-blocker already, why aren't you? I'm serious.
Host level ad-blocker:
- uBlock Origin for all browsers
- AdGuard for Desktop (Windows, MacOS)
- AdGuard for Mobile (iOS and Android)
- PortMaster + (DNS ad-list) for Windows
- Little Snitch + (DNS ad-list) for MacOS
- etc
Network level ad-blocker:
- Pi-hole
- AdGuard Home (my current choice)
- etc
Another day, another company tracking over 5 billion of users worldwide.
A recent investigation by 404 Media has unveiled details about a secretive spy tool called Patternz, which monitors billions of phone profiles through the advertising industry.
Full report:

Inside a Global Phone Spy Tool Monitoring Billions
A wide-spanning investigation by 404 Media reveals more details about a secretive spy tool that can tracks billions of phone profiles through the advertising industry called Patternz. Google has taken action in response to 404 Media's inquiries.
The Patternz tool provides detailed information about users, including GPS coordinates, frequently visited locations, hobbies, and interests.
Google has known Patternz since at least June 2021, and worked with them until this week, where Google has terminated their account, due to this investigation.
In response to inquiries from 404 Media, Google and another ad firm, PubMatic, have cut off a company linked to the surveillance firm.
The investigation provides one of the clearest examinations yet of how advertisements in ordinary mobile apps can ultimately lead to surveillance by spy firms and their government clients through the real-time bidding data supply chain.
Personal opinion:
Yes, you're being tracked without your consent or knowledge, simply by using services/apps that have ads. These ad networks, then aggregate and correlate information on a worldwide level.
We don't have to make it easy for these companies to gather this data.
If you're not using a host-based and/or network-based ad-blocker already, why aren't you? I'm serious.
Host level ad-blocker:
- uBlock Origin for all browsers
- AdGuard for Desktop (Windows, MacOS)
- AdGuard for Mobile (iOS and Android)
- PortMaster + (DNS ad-list) for Windows
- Little Snitch + (DNS ad-list) for MacOS
- etc
Network level ad-blocker:
- Pi-hole
- AdGuard Home (my current choice)
- etc
- Joined
- Feb 23, 2016
- Messages
- 21,522
- Likes
- 39,237
You know this I think, but just a note that Chrome on Android will not let you use uBlock Origin. So if you wish to use it you need to use another browser on Android. Brave, Firefox, Firefox Focus, Vivaldi, DuckDuckGo browser and others.
Similar threads
- Replies
- 2
- Views
- 2K
- Replies
- 105
- Views
- 17K
