Where did you find that advice? I've not seen anything like that, especially as windows in now patched.So I'd avoid using Win10 for browsing for a while but the risk is far lower for other platforms.
-
WANTED: Happy members who like to discuss audio and other topics related to our interest. Desire to learn and share knowledge of science required. There are many reviews of audio hardware and expert members to help answer your questions. Click here to have your audio equipment measured for free!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Intel Kernel Bug
- Thread starter DonH56
- Start date
-
- Tags
- intel cpu kernel bug
View attachment 9977
Not enabled by default on 57.0.4 build for either my Linux or Win10 installs here?
I'll try it on the Win10 I use for finance to see if it interferes with connections to my banks, etc.
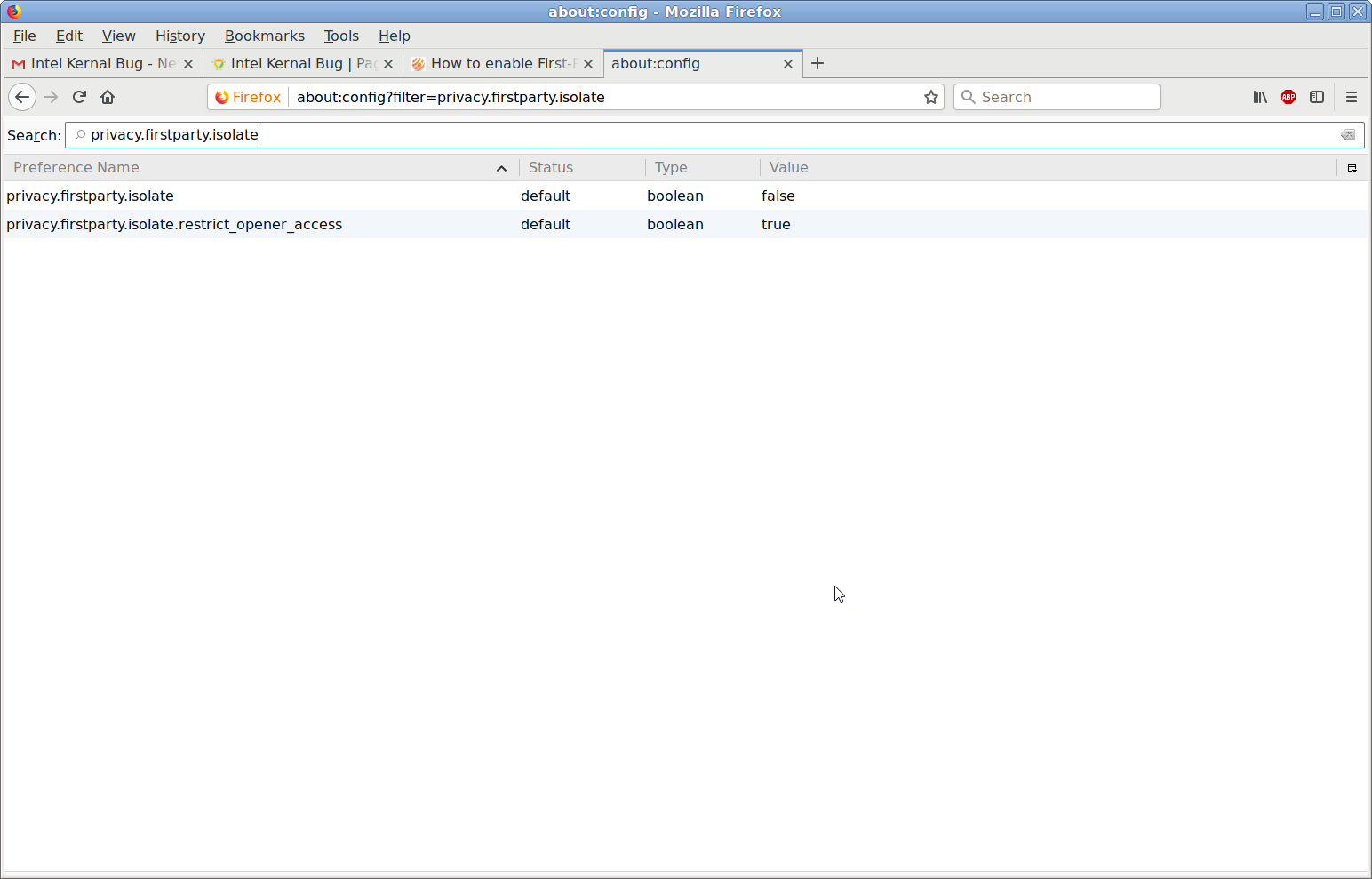
"WARNING, This might void your warranty!" LOL, what warranty?Similar is also available for firefox, see https://www.ghacks.net/2017/11/22/how-to-enable-first-party-isolation-in-firefox/ it might be on by default now as I belive firefix was patched for what they could do against this the other day.
Not enabled by default on 57.0.4 build for either my Linux or Win10 installs here?
I'll try it on the Win10 I use for finance to see if it interferes with connections to my banks, etc.
Logged into my main bank and a few other sites without issue. Will see what happens for a bit.I'll try it on the Win10 I use for finance to see if it interferes with connections to my banks, etc.
Site isolation should not cause any compatibility problems. It just slows down certain scenarios.
D
Deleted member 65
Guest
To be fully protected from Meltdown&Spectre on Intel/Windows 10 you need two patches:
1. Microsoft KB4056892 (OS Build 16299.192) Windows 10 version 1709.
2. Intel CPU microcode update. Needs to be applied through a BIOS update.
1. Microsoft KB4056892 (OS Build 16299.192) Windows 10 version 1709.
2. Intel CPU microcode update. Needs to be applied through a BIOS update.
Linux kernel updates should now be available for most distributions.
PCLinuxOS updates available as of last night.
PCLinuxOS updates available as of last night.
On this point, Intel has a tool that quickly tells you if your system is without this patch: https://downloadcenter.intel.com/download/27150?v=t2. Intel CPU microcode update. Needs to be applied through a BIOS update.
Run the Discovery tool.gui after it extracts the zip.
I just ran it and as I expected, my system is vulnerable because HP has yet to release this patch!
- Thread Starter
- #48
BIOS updates are likely to be painful... They normally have to do a lot of regression testing before release (not that OS' don't). Bet a lot of folk are losing a lot of sleep right now. And updating the BIOS on a server is painful.
Apparently Dell has already released their patch and Microsoft did the same in the OS upgrade for Surface. What is a pain is that there is no information from HP in my search. They should provide information as to when the fix maybe forthcoming.
- Thread Starter
- #50
My Dell work PC is managed by our IT and is vulnerable, has not been updated yet. I'll have to check on my Dell home computer. I'd be very surprised if the patch was available for all systems (I have PCs at home from 1 to ~7+ years old still running).
https://www.engadget.com/2018/01/08/intel-meltdown-spectre-flaw-security-patch/
Intel will patch all recent chips by the end of January
90 percent of recent processors affected by Meltdown/Spectre will see fixes this week.
Intel, which to date is the company most affected by the exploits, already committed to patching "90 percent" of affected processors made in the past five years by the end of this week. Today on stage at CES, Intel CEO Brian Krzanich promised the remaining 10 percent would see fixes by the end of the month.
"We believe the performance impact of these updates is highly workload dependent," Krzanich said, referring to claims that processors may be slowed by as much as 30 percent as a result of the fixes. "We expect some may have a larger impact than others, so we'll continue working with the industry to minimize the impact on those workloads over time."
Krzanich reiterated Intel's stance that there's no evidence either exploit has been used to steal customer data, and said the company is "working tirelessly on these issues to ensure it stays that way."
There's still no word on a timeline for when affected processors made over five years ago will be patched.
Intel will patch all recent chips by the end of January
90 percent of recent processors affected by Meltdown/Spectre will see fixes this week.
Intel, which to date is the company most affected by the exploits, already committed to patching "90 percent" of affected processors made in the past five years by the end of this week. Today on stage at CES, Intel CEO Brian Krzanich promised the remaining 10 percent would see fixes by the end of the month.
"We believe the performance impact of these updates is highly workload dependent," Krzanich said, referring to claims that processors may be slowed by as much as 30 percent as a result of the fixes. "We expect some may have a larger impact than others, so we'll continue working with the industry to minimize the impact on those workloads over time."
Krzanich reiterated Intel's stance that there's no evidence either exploit has been used to steal customer data, and said the company is "working tirelessly on these issues to ensure it stays that way."
There's still no word on a timeline for when affected processors made over five years ago will be patched.
- Thread Starter
- #52
Hmmm... Forgot to check on my home Dell desktop, but my MSI notebook is not vulnerable, and AFAIK has not had a BIOS update.
D
Deleted member 65
Guest
List of affected Intel CPU's, if I read table correct my Dell Laptops Intel Core i7 4702 22nm is not one of the affected CPU's.
Intel® Core™ i3 processor (45nm and 32nm) Intel® Core™ i5 processor (45nm and 32nm) Intel® Core™ i7 processor (45nm and 32nm) Intel® Core™ M processor family (45nm and 32nm) 2nd generation Intel® Core™ processors 3rd generation Intel® Core™ processors 4th generation Intel® Core™ processors 5th generation Intel® Core™ processors 6th generation Intel® Core™ processors 7th generation Intel® Core™ processors 8th generation Intel® Core™ processors Intel® Core™ X-series Processor Family for Intel® X99 platforms Intel® Core™ X-series Processor Family for Intel® X299 platforms Intel® Xeon® processor 3400 series Intel® Xeon® processor 3600 series Intel® Xeon® processor 5500 series Intel® Xeon® processor 5600 series Intel® Xeon® processor 6500 series Intel® Xeon® processor 7500 series Intel® Xeon® Processor E3 Family Intel® Xeon® Processor E3 v2 Family Intel® Xeon® Processor E3 v3 Family Intel® Xeon® Processor E3 v4 Family Intel® Xeon® Processor E3 v5 Family Intel® Xeon® Processor E3 v6 Family Intel® Xeon® Processor E5 Family Intel® Xeon® Processor E5 v2 Family Intel® Xeon® Processor E5 v3 Family Intel® Xeon® Processor E5 v4 Family Intel® Xeon® Processor E7 Family Intel® Xeon® Processor E7 v2 Family Intel® Xeon® Processor E7 v3 Family Intel® Xeon® Processor E7 v4 Family Intel® Xeon® Processor Scalable Family Intel® Xeon Phi™ Processor 3200, 5200, 7200 Series Intel® Atom™ Processor C Series Intel® Atom™ Processor E Series Intel® Atom™ Processor A Series Intel® Atom™ Processor x3 Series Intel® Atom™ Processor Z Series Intel® Celeron® Processor J Series Intel® Celeron® Processor N Series Intel® Pentium® Processor J Series Intel® Pentium® Processor N Series
Read more: https://www.tweaktown.com/news/60411/heres-list-intel-cpus-affected-spectre-meltdown/index.html
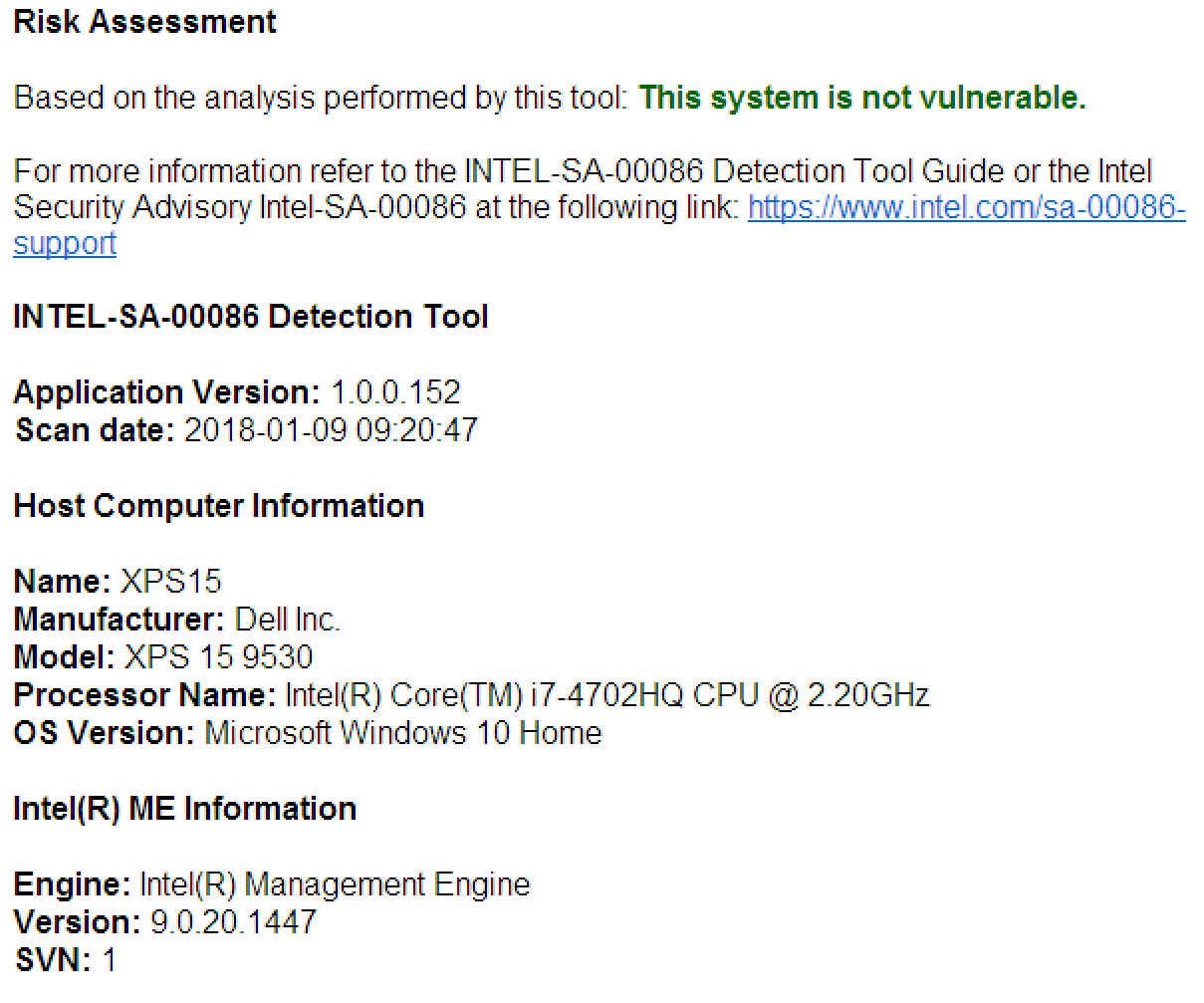
Edit/Update: Performed the test on my SilentPC i7/8700 CPU where I have not yet applied the new Asus BIOS with the Intel CPU Microcode update.
The Intel SW deemed PC as Not vulnerable! Seems as if the app only tests whether the MS SW patch has been applied & not the CPU microcode update.
Intel® Core™ i3 processor (45nm and 32nm) Intel® Core™ i5 processor (45nm and 32nm) Intel® Core™ i7 processor (45nm and 32nm) Intel® Core™ M processor family (45nm and 32nm) 2nd generation Intel® Core™ processors 3rd generation Intel® Core™ processors 4th generation Intel® Core™ processors 5th generation Intel® Core™ processors 6th generation Intel® Core™ processors 7th generation Intel® Core™ processors 8th generation Intel® Core™ processors Intel® Core™ X-series Processor Family for Intel® X99 platforms Intel® Core™ X-series Processor Family for Intel® X299 platforms Intel® Xeon® processor 3400 series Intel® Xeon® processor 3600 series Intel® Xeon® processor 5500 series Intel® Xeon® processor 5600 series Intel® Xeon® processor 6500 series Intel® Xeon® processor 7500 series Intel® Xeon® Processor E3 Family Intel® Xeon® Processor E3 v2 Family Intel® Xeon® Processor E3 v3 Family Intel® Xeon® Processor E3 v4 Family Intel® Xeon® Processor E3 v5 Family Intel® Xeon® Processor E3 v6 Family Intel® Xeon® Processor E5 Family Intel® Xeon® Processor E5 v2 Family Intel® Xeon® Processor E5 v3 Family Intel® Xeon® Processor E5 v4 Family Intel® Xeon® Processor E7 Family Intel® Xeon® Processor E7 v2 Family Intel® Xeon® Processor E7 v3 Family Intel® Xeon® Processor E7 v4 Family Intel® Xeon® Processor Scalable Family Intel® Xeon Phi™ Processor 3200, 5200, 7200 Series Intel® Atom™ Processor C Series Intel® Atom™ Processor E Series Intel® Atom™ Processor A Series Intel® Atom™ Processor x3 Series Intel® Atom™ Processor Z Series Intel® Celeron® Processor J Series Intel® Celeron® Processor N Series Intel® Pentium® Processor J Series Intel® Pentium® Processor N Series
Read more: https://www.tweaktown.com/news/60411/heres-list-intel-cpus-affected-spectre-meltdown/index.html
Edit/Update: Performed the test on my SilentPC i7/8700 CPU where I have not yet applied the new Asus BIOS with the Intel CPU Microcode update.
The Intel SW deemed PC as Not vulnerable! Seems as if the app only tests whether the MS SW patch has been applied & not the CPU microcode update.
Last edited by a moderator:
I have the Microsoft Windows 10 patch and it still says my system is vulnerable.
- Thread Starter
- #56
Just checked my Dell desktop and the Intel program says it is not vulnerable, has already been patched. I did a BIOS update a few days ago so maybe that was it?
Must have been. Or else the tool is faulty! 
- Thread Starter
- #58
Shhh!
This is while booted into my Linux workstation on my desktop system running the latest patched kernel?
[root@localhost SA00086_Linux]# python ./intel_sa00086.py
INTEL-SA-00086 Detection Tool
Copyright(C) 2017, Intel Corporation, All rights reserved
Application Version: 1.0.0.152
Scan date: 2018-01-10 05:48:09 GMT
*** Host Computer Information ***
Name: localhost.localdomain
Manufacturer: Gigabyte Technology Co., Ltd.
Model: EP45-UD3P
Processor Name: Intel(R) Core(TM)2 Quad CPU Q9550 @ 2.83GHz
OS Version: PCLinuxOS 2018 PCLinuxOS (4.14.12-pclos1)
*** Risk Assessment ***
Detection Error: This system may be vulnerable,
either the Intel(R) MEI/TXEI driver is not installed
(available from your system manufacturer)
or the system manufacturer does not permit access
to the ME/TXE from the host driver.
For more information refer to the INTEL-SA-00086 Detection Tool Guide or the
Intel Security Advisory Intel-SA-00086 at the following link:
https://www.intel.com/sa-00086-support
[root@localhost SA00086_Linux]#
[root@localhost SA00086_Linux]# python ./intel_sa00086.py
INTEL-SA-00086 Detection Tool
Copyright(C) 2017, Intel Corporation, All rights reserved
Application Version: 1.0.0.152
Scan date: 2018-01-10 05:48:09 GMT
*** Host Computer Information ***
Name: localhost.localdomain
Manufacturer: Gigabyte Technology Co., Ltd.
Model: EP45-UD3P
Processor Name: Intel(R) Core(TM)2 Quad CPU Q9550 @ 2.83GHz
OS Version: PCLinuxOS 2018 PCLinuxOS (4.14.12-pclos1)
*** Risk Assessment ***
Detection Error: This system may be vulnerable,
either the Intel(R) MEI/TXEI driver is not installed
(available from your system manufacturer)
or the system manufacturer does not permit access
to the ME/TXE from the host driver.
For more information refer to the INTEL-SA-00086 Detection Tool Guide or the
Intel Security Advisory Intel-SA-00086 at the following link:
https://www.intel.com/sa-00086-support
[root@localhost SA00086_Linux]#
Looks like you need the Intel MEI driver as it states.
Similar threads
- Replies
- 47
- Views
- 8K
- Replies
- 4
- Views
- 551
- Replies
- 92
- Views
- 12K
- Replies
- 56
- Views
- 6K
